VPN instances are used to isolate VPN routes from public network
routes. Configuring VPN instances is required in all MPLS L3VPN
networking schemes.
In addition, routes of a VPN instance are isolated from those of another. This feature allows VPN instances to be used in networking schemes other than MPLS L3VPNs.
All VPN instance configurations are on PEs.
Creating a VPN Instance
A VPN
instance is associated with a site, rather than a VPN. It is a
collection of the VPN membership and routing rules of its associated
site.
A VPN instance takes effect only after you configure an RD for it. Before configuring an RD for a VPN instance, you can configure no parameters for the instance other than a description.
A VPN instance description is a piece of descriptive information about the VPN instance. You can use it to keep information such as the relationship of the VPN instance with a VPN.
Follow these steps to create and configure a VPN instance:
Note:
The maximum number of VPN instances that can be configured on a PE varies by device.
Associating a VPN Instance with an Interface
After creating and configuring a VPN instance, you associate the VPN instance with the interface for connecting CEs. Any interface supporting MPLS LDP capability can be associated with a VPN instance. For interfaces supporting MPLS LDP capability, refer to MPLS Basics Configuration in the MPLS Volume.
Follow these steps to associate a VPN instance with an interface:
Note:
When configured on an interface, the ip binding vpn-instance command clears the IP address of the interface. Therefore, you must re-configure the IP address of the interface after configuring the command.
The control process of VPN route advertisement is as follows:
Follow these steps to configure route related attributes of a VPN instance
In addition, routes of a VPN instance are isolated from those of another. This feature allows VPN instances to be used in networking schemes other than MPLS L3VPNs.
All VPN instance configurations are on PEs.
Creating a VPN Instance
A VPN instance takes effect only after you configure an RD for it. Before configuring an RD for a VPN instance, you can configure no parameters for the instance other than a description.
A VPN instance description is a piece of descriptive information about the VPN instance. You can use it to keep information such as the relationship of the VPN instance with a VPN.
Follow these steps to create and configure a VPN instance:
Note:
The maximum number of VPN instances that can be configured on a PE varies by device.
Associating a VPN Instance with an Interface
After creating and configuring a VPN instance, you associate the VPN instance with the interface for connecting CEs. Any interface supporting MPLS LDP capability can be associated with a VPN instance. For interfaces supporting MPLS LDP capability, refer to MPLS Basics Configuration in the MPLS Volume.
Follow these steps to associate a VPN instance with an interface:
Note:
When configured on an interface, the ip binding vpn-instance command clears the IP address of the interface. Therefore, you must re-configure the IP address of the interface after configuring the command.
Configuring Route Related Attributes of a VPN Instance
- When a VPN route learned from a CE gets redistributed into BGP, BGP associates it with a VPN target extended community attribute list, which is usually the export target attribute of the VPN instance associated with the CE.
- The VPN instance determines which routes it can accept and redistribute according to the import-extcommunity in the VPN target.
- The VPN instance determines how to change the VPN targets attributes for routes to be redistributed according to the export-extcommunity in the VPN target.
Follow these steps to configure route related attributes of a VPN instance
Note:
- A single vpn-target command can configure up to eight VPN targets. You can configure up to 20 VPN targets for a VPN instance.
- You
can define the maximum number of routes for a VPN instance to support,
preventing too many routes from being redistributed into the PE. The
maximum number of routes supported by a PE varies by device.
- Before
associating a routing policy with a VPN instance, you must create the
routing policy at first. Otherwise, the default routing policy is used.
Configuring a Tunneling Policy of a VPN Instance
I. Configuring a tunneling policy
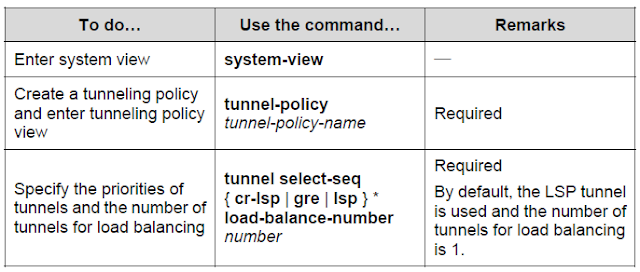
Follow these steps to configure a tunneling policy:
Note:
- Support for GRE tunneling depends on the device model.
- When
you configure tunnel priorities using the tunnel select-seq command, a
tunnel type closer to the select-seq keyword has a higher priority. For
example, with the tunnel select-seq lsp gre load-balance-number 1
command configured, VPN uses a GRE tunnel if no LSP exists. Once an LSP
is created, the LSP tunnel is used instead.
- If
you specify more than one tunnel type and the number of tunnels of a
type is less than the specified number of tunnels for load balance,
tunnels of different types may be used.
II. Associating a tunneling policy with the VPN instance
Follow these steps to associate a tunneling policy with the VPN instance:
Note:
Create the tunneling policy before associating it with the VPN instance. Otherwise, the default policy will be used.
Configuring a Tunneling Policy of a VPN Instance
I. Configuring a tunneling policy
Follow these steps to configure a tunneling policy:
Note:
- Support for GRE tunneling depends on the device model.
- When you configure tunnel priorities using the tunnel select-seq command, a tunnel type closer to the select-seq keyword has a higher priority. For example, with the tunnel select-seq lsp gre load-balance-number 1 command configured, VPN uses a GRE tunnel if no LSP exists. Once an LSP is created, the LSP tunnel is used instead.
- If you specify more than one tunnel type and the number of tunnels of a type is less than the specified number of tunnels for load balance, tunnels of different types may be used.
II. Associating a tunneling policy with the VPN instance
Follow these steps to associate a tunneling policy with the VPN instance:
Note:
Create the tunneling policy before associating it with the VPN instance. Otherwise, the default policy will be used.




No comments:
Post a Comment